
Website Security
Secure your site or recover a site that has been hacked
Support Plans
We can keep your website up to date or play a larger role in the team.
Recent Blog Posts
How AI Generated Text and Images Are Revolutionizing Web Design
Written by Chris on . Posted in Artificial Intelligence
AI is a hot topic. Fear, excitement, the whole shebang. As AI-generated text and images become increasingly sophisticated, they're opening up new possibilities and revolutionizing the way we approach web design. Let's dive into how AI-generated content is changing the game and what it means for the future of web design.

The Future of Web Design: Key Trends and Predictions for 2023 and Beyond
Written by Chris on . Posted in Web Design
Hello, tech enthusiasts! It's me, Chris. Let's do some diving into the fascinating world of web design and exploring the latest trends that are shaping the industry. As we journey through 2023, we're taking a closer look at the future of web design and the innovative trends that are emerging. Let's delve into the key trends and predictions for 2023 and beyond.
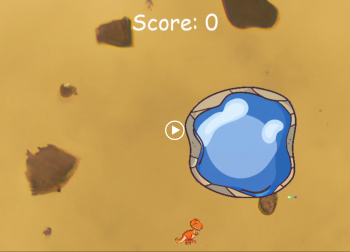
AI Created This Game
Written by Chris on . Posted in Artificial Intelligence
Machine learning is able to create computer code. It can create images. Put these together and have AI create an entire playable game. This video shows that AI-made game being played.
Beachside Technology
 WordPress design, web development, email setup and tech support in Vero Beach, Florida. My name is Chris. Call me!
WordPress design, web development, email setup and tech support in Vero Beach, Florida. My name is Chris. Call me!Phone: 772-410-4879
[email protected]
Contact Form
Recent Posts
- A Step-by-Step Guide to Setting Up and Securing Your Business Email
- Top 5 Signs That Your Computer Needs Repair or an Upgrade
- Essential Computer Maintenance Tips to Keep Your System Running Smoothly
- How AI Generated Text and Images Are Revolutionizing Web Design
- The Future of Web Design: Key Trends and Predictions for 2023 and Beyond
Web Hosting
We swear by WP Engine Web Hosting.


Beachside Technology
Vero Beach, Florida
Phone: 772-410-4879
[email protected]
Terms of Service
Review Us!
Remote Support